Open Source Okta Alternatives
A curated collection of the 7 best open source alternatives to Okta.
The best open source alternative to Okta is Authentik. If that doesn't suit you, we've compiled a ranked list of other open source Okta alternatives to help you find a suitable replacement. Other interesting open source alternatives to Okta are: SuperTokens, Ory, Logto and Hanko.
Okta alternatives are mainly Auth & SSO Tools but may also be Security Tools or Developer Tools. Browse these if you want a narrower list of alternatives or looking for a specific functionality of Okta.
authentik is an open-source identity provider that offers self-hosted authentication, authorization, and user management for businesses of all sizes.
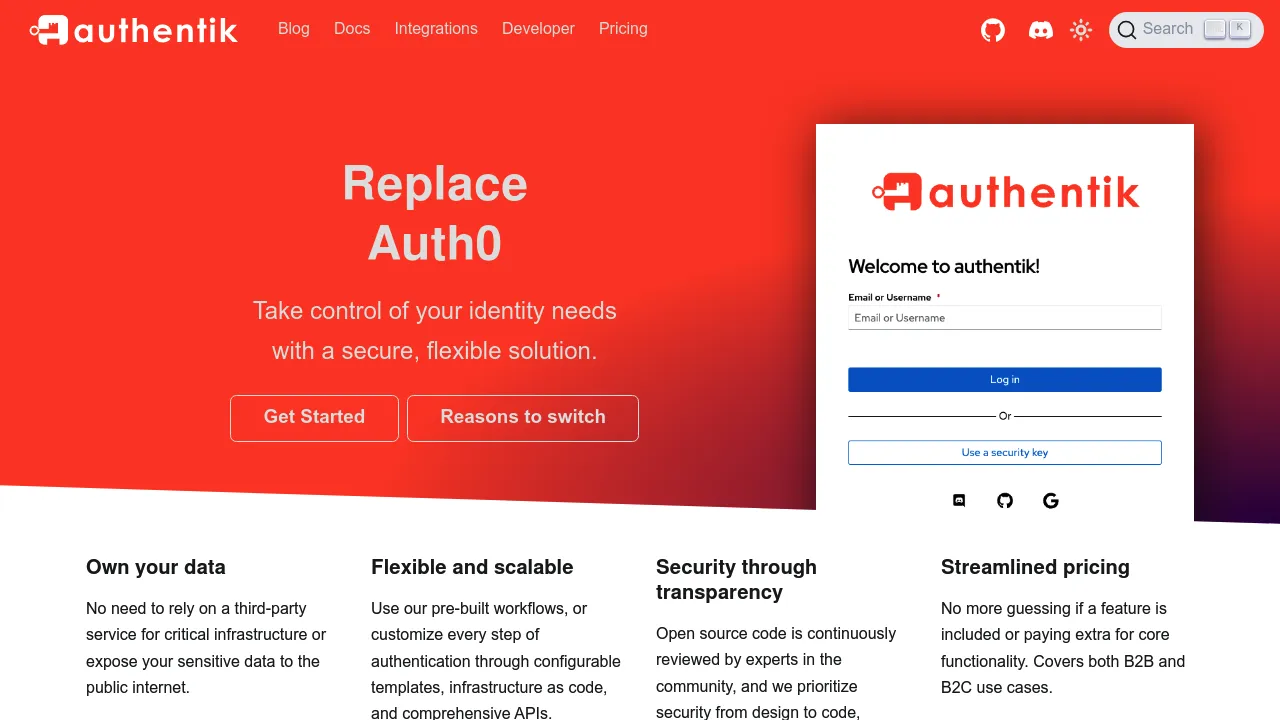
authentik is a powerful, open-source identity and access management solution designed to give organizations full control over their authentication and authorization needs. Here's why authentik stands out:
-
Self-hosted and Open Source:
- Deploy anywhere, maintaining complete control over your sensitive data
- Continuously reviewed by community experts, ensuring transparency and security
-
Flexible and Customizable:
- Pre-built workflows for quick setup
- Fully customizable authentication steps through configurable templates
- Comprehensive APIs for advanced automation
-
Enterprise-Grade Features:
- Multi-factor authentication (MFA)
- Conditional access
- Application proxy
- Support for multiple protocols (SAML2, OAuth2, OIDC, SCIM, LDAP, RADIUS)
-
Scalable and Easy to Deploy:
- Supports Kubernetes, Terraform, and Docker Compose
- Designed for both B2B and B2C use cases
-
Comprehensive Identity Solution:
- Authentication
- User enrollment
- Self-service capabilities
-
Cost-Effective:
- Streamlined pricing with no hidden costs
- Core functionality included without extra charges
authentik empowers organizations to prioritize security, simplify deployment, and automate identity workflows. Whether you're a small business or a large enterprise, authentik provides the tools and flexibility to meet your specific identity and access management needs.
Open-source authentication solution offering flexible, self-hosted user management with advanced features and easy integration.
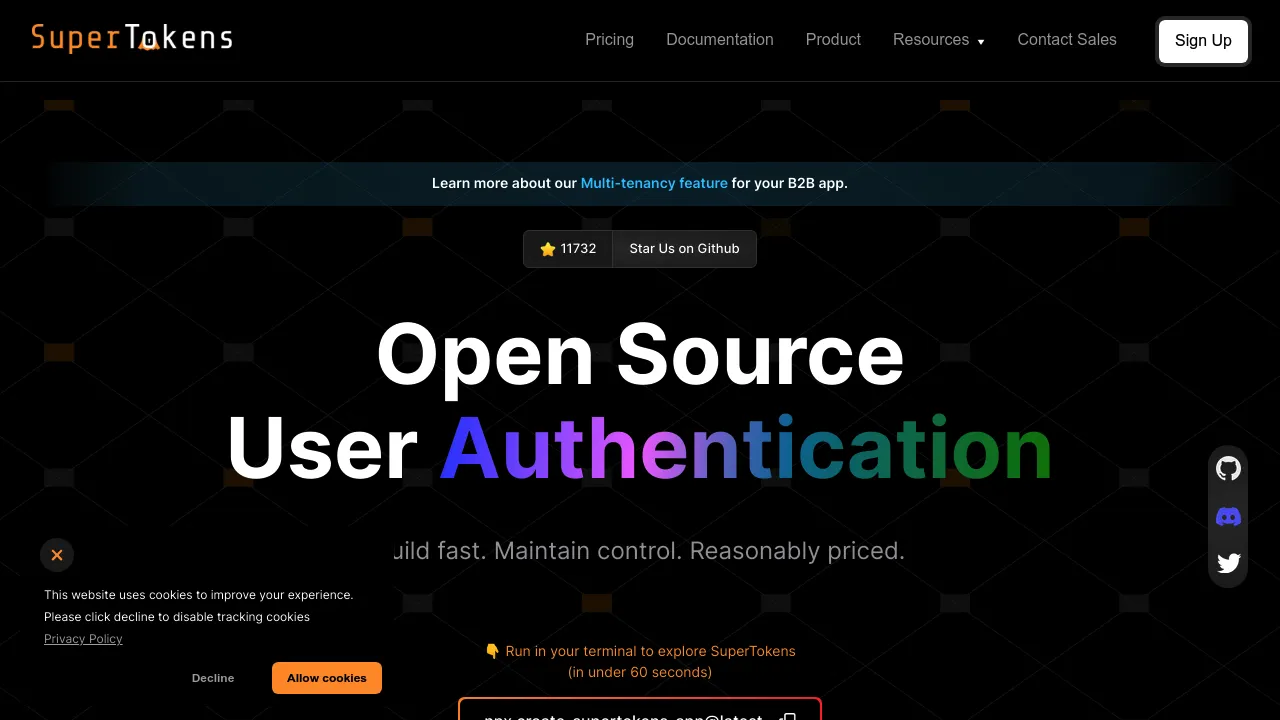
SuperTokens is an open-source authentication solution that provides developers with a powerful, flexible, and secure way to implement user management in their applications. With SuperTokens, you can easily add robust authentication features to your web and mobile apps while maintaining full control over your user data.
Key benefits of SuperTokens include:
- Self-hosted: Keep your user data on your own servers, ensuring complete data ownership and privacy compliance.
- Customizable: Tailor the authentication flow and UI to match your brand and specific requirements.
- Multi-tenancy support: Easily manage multiple apps or organizations within a single instance.
- Comprehensive features: Includes session management, social logins, passwordless auth, and more out of the box.
- Language agnostic: Supports various backend languages and frameworks, making it versatile for different tech stacks.
- Active community: Benefit from continuous improvements, updates, and support from a growing open-source community.
- Easy integration: Well-documented SDKs and APIs make implementation straightforward for developers.
- Scalable: Designed to handle high traffic and grow with your application's needs.
By choosing SuperTokens, you're not just getting an authentication solution; you're gaining a flexible, secure, and future-proof foundation for your user management needs. Whether you're building a small project or a large-scale application, SuperTokens provides the tools and flexibility to create a seamless authentication experience for your users.
Ory is a certified and battle-tested identity solution backed by a large open source community and trusted by Fortune 500 companies.
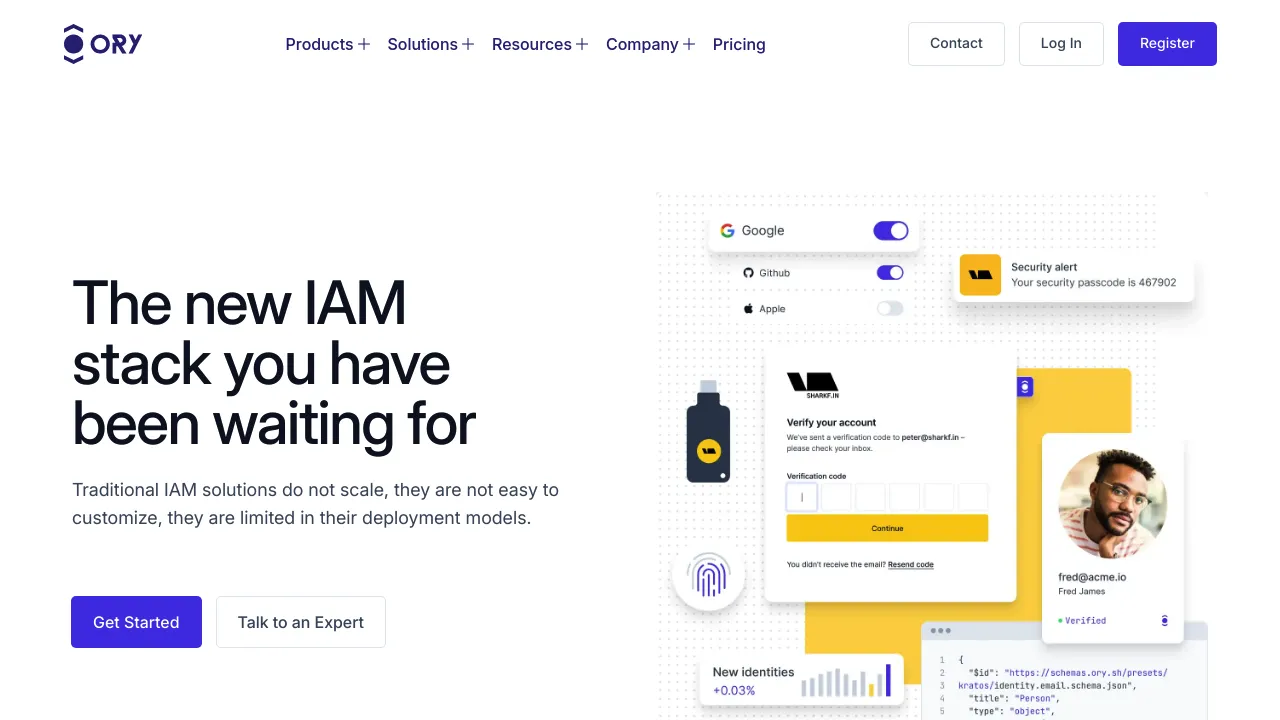
Ory provides a modern and modular approach to identity and access management (IAM) that scales, offers unmatched user experience and deployment flexibility, and only charges for what is used.
Key benefits of Ory include:
- Uninterrupted performance even under demanding conditions, ensuring no revenue loss during peak demand
- Comprehensive visibility and fully configurable options to balance user experience, privacy and security
- Unmatched flexibility for customization beyond just branding, including UI, workflows, standards, deployment, scale and security
- Integrations and SDKs for all modern and legacy frameworks
- Migration guides to easily move from home-grown or other IAM solutions
- Trusted by over 30,000 companies, from startups to Fortune 500 enterprises
- Available as open source, self-hosted, or fully managed cloud offering
Ory allows you to build a unified identity system that meets all your needs, whether you're looking for authentication, authorization, user management, or a complete IAM platform. With options for self-hosting or using the managed Ory Network, you can get started quickly and scale seamlessly as your needs grow.
An open-source identity solution offering customizable login experiences, multi-tenant support, and comprehensive user management.
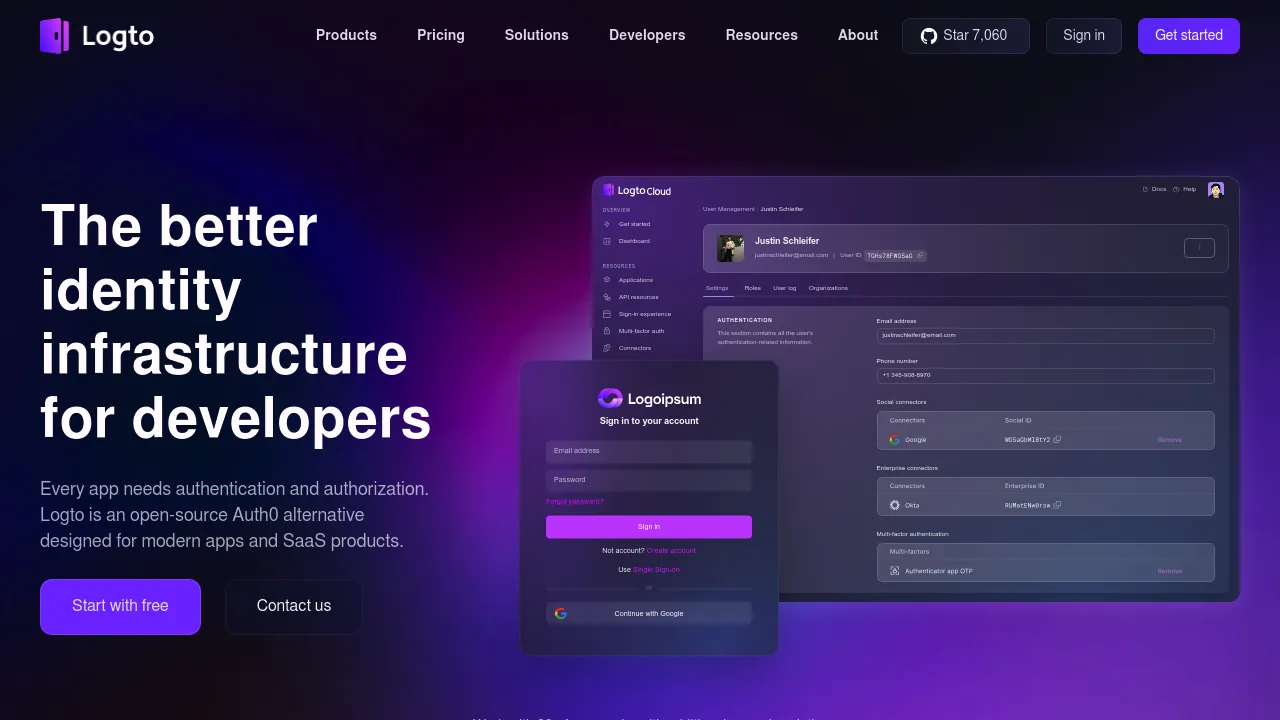
Logto is a powerful, open-source identity platform designed to simplify authentication and user management for modern applications. With its robust features and flexible architecture, Logto enables developers to implement secure, seamless authentication flows while providing an exceptional user experience.
Key benefits of Logto include:
- Customizable login experiences: Tailor the authentication process to match your brand and user preferences, creating a cohesive and engaging login flow.
- Multi-tenant support: Easily manage multiple applications and organizations within a single Logto instance, streamlining your identity infrastructure.
- Comprehensive user management: Gain full control over user data, roles, and permissions with intuitive tools for efficient user administration.
- Enterprise-grade security: Implement industry-standard security protocols and best practices to protect user identities and sensitive information.
- Extensible architecture: Integrate Logto seamlessly with your existing tech stack and extend its functionality through a wide range of connectors and APIs.
- Open-source advantage: Benefit from community-driven development, transparency, and the ability to customize the solution to your specific needs.
Whether you're building a small application or managing a complex ecosystem of services, Logto provides the tools and flexibility to create secure, user-friendly authentication experiences that scale with your business.
Streamline user authentication with passwordless login, enhancing security and user experience for your web applications.
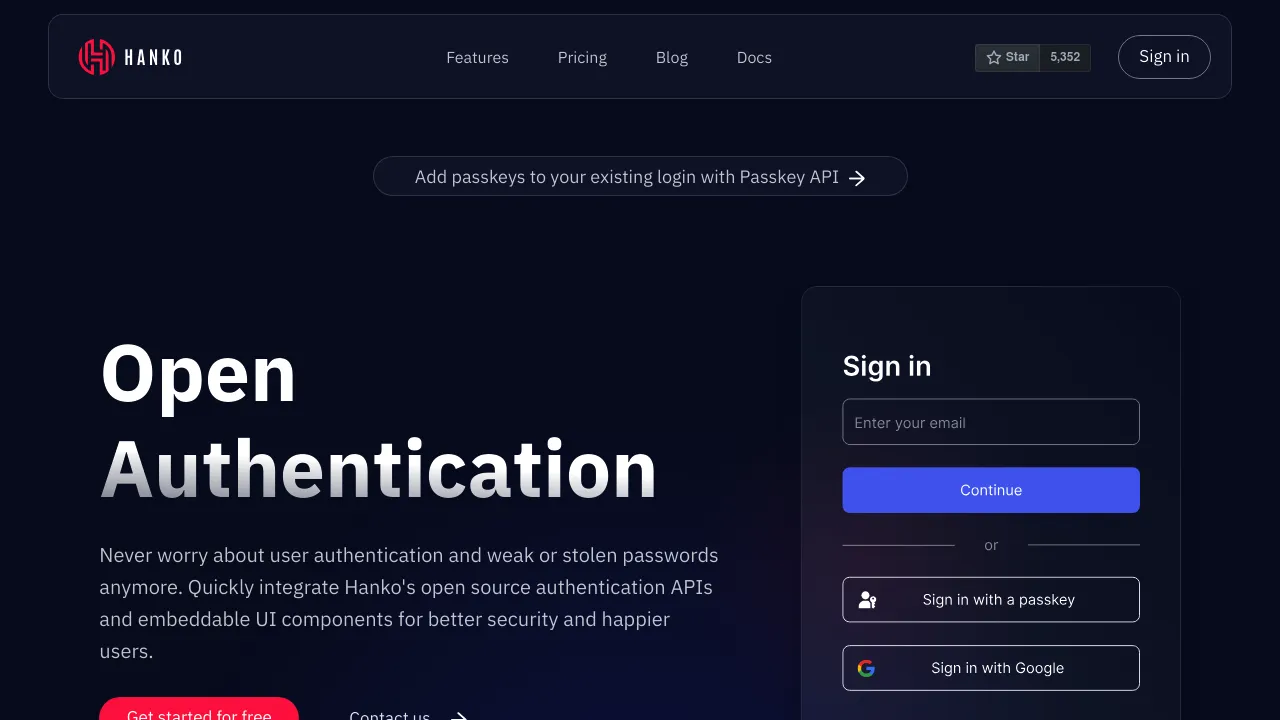
Hanko is a cutting-edge authentication solution designed to revolutionize the way users access web applications. By embracing passwordless technology, Hanko offers a seamless and secure login experience that benefits both developers and end-users alike.
Key benefits of Hanko include:
- Enhanced Security: Eliminate password-related vulnerabilities and reduce the risk of account breaches.
- Improved User Experience: Provide a frictionless login process, increasing user satisfaction and retention.
- Easy Integration: Implement Hanko quickly with pre-built components and comprehensive documentation.
- Customization Options: Tailor the authentication flow to match your brand and application requirements.
- Multi-factor Authentication: Strengthen security with additional factors like biometrics or security keys.
- GDPR Compliance: Ensure user data privacy with built-in compliance features.
- Open Source Transparency: Benefit from community-driven development and security audits.
Hanko empowers developers to create secure, user-friendly applications without the hassle of managing complex authentication systems. By leveraging modern web standards and best practices, Hanko paves the way for a passwordless future, making online interactions safer and more convenient for everyone.
Streamline API authentication with UnKey's powerful, developer-friendly platform for creating, revoking, and monitoring API keys.

UnKey revolutionizes API key management, offering developers a robust and user-friendly solution for securing and scaling their applications. With UnKey, you can effortlessly create, revoke, and monitor API keys, ensuring optimal control over access to your services.
Key benefits of UnKey include:
- Simplified Key Management: Create and manage API keys with ease, streamlining your development workflow.
- Enhanced Security: Implement robust authentication measures to protect your APIs from unauthorized access.
- Real-time Monitoring: Gain valuable insights into API key usage, helping you identify potential issues and optimize performance.
- Scalability: Designed to grow with your application, UnKey handles millions of requests without breaking a sweat.
- Developer-Friendly: Intuitive APIs and comprehensive documentation make integration a breeze.
- Customizable Permissions: Fine-tune access control with granular permission settings for each API key.
- Automatic Key Rotation: Enhance security with scheduled key rotations, reducing the risk of compromised credentials.
- Usage Analytics: Make data-driven decisions with detailed analytics on API key usage patterns.
Whether you're a solo developer or part of a large team, UnKey provides the tools you need to manage API authentication efficiently and securely. Say goodbye to the headaches of traditional key management and hello to a more streamlined, powerful approach with UnKey.
Comprehensive suite of enterprise-grade security and compliance tools for SaaS applications, enhancing data protection and user management.
BoxyHQ provides a robust set of enterprise-ready features designed to elevate SaaS applications to meet the stringent security and compliance requirements of large organizations. By integrating BoxyHQ, developers can quickly implement essential enterprise functionalities without the need for extensive custom development.
Key benefits of BoxyHQ include:
- Enhanced Security: Implement Single Sign-On (SSO) and Multi-Factor Authentication (MFA) to strengthen access controls and protect sensitive data.
- Compliance Made Easy: Achieve and maintain compliance with industry standards like SOC2, HIPAA, and GDPR through built-in audit logs and data access controls.
- Simplified User Management: Streamline user provisioning and deprovisioning with SCIM, reducing administrative overhead and improving security.
- Data Residency Solutions: Address data sovereignty concerns with flexible data storage options, ensuring compliance with regional regulations.
- Developer-Friendly Integration: Utilize well-documented APIs and SDKs for seamless integration into existing SaaS architectures.
- Cost-Effective Scaling: Reduce development time and resources required to build enterprise-grade features, allowing faster time-to-market for enterprise customers.
By leveraging BoxyHQ, SaaS providers can confidently serve enterprise clients, offering the security and compliance features they demand while focusing on their core product offerings.
Discover Open Source alternatives to:
View all alternativesAirtable
A cloud-based platform that combines the simplicity of a spreadsheet with the complexity of a database for organizing data.
Typeform
An online form builder with a user-friendly interface that allows businesses to create engaging and interactive forms, surveys, quizzes, and more with a focus on a conversational experience.
Notion
An all-in-one workspace for note-taking, project management, knowledge sharing, and collaboration across teams.
Monday
An all-in-one project management tool and suite of products for teams.
Fathom Analytics
A Google Analytics alternative that’s simple & privacy-first. Experience ease of use, forever data retention & full legal compliance.
Todoist
The world's favorite task manager and to-do list app. Finally become focused, organized and calm.